I recently installed Postfix + SpamAssassin at a customer as a front end to MS Exchange, and they are reporting that alerts from CBS Marketwatch are being garbled. This apparently didn't happen with the previous sendmail front end, so I've been tasked to figure it out. I believe that neither SpamAssassin nor Postfix are messing anything up, but it's necessary to prove it. This is how we're doing so.
The first step was to modify the postfix filter that runs the mail through SpamAssassin and capture the emails before and after processing. We modified the /etc/postfix/spamassassin-filter.sh script
#!/bin/sh
# Localize these.
INSPECT_DIR=/var/spool/filter
SENDMAIL="/usr/sbin/sendmail -i"
# Exit codes from <sysexits.h>
EX_TEMPFAIL=75
EX_UNAVAILABLE=69
# Clean up when done or when aborting.
# trap "rm -f in.$$ out.$$" 0 1 2 3 15
# Start processing.
cd $INSPECT_DIR || { echo $INSPECT_DIR does not exist; exit $EX_TEMPFAIL; }
echo "$$: running $@" >> filter.log
tee in.$$ |
/usr/local/bin/spamc > out.$$ || {
echo "Message content rejected"; exit $EX_UNAVAILABLE; }
$SENDMAIL "$@" <out.$$
exit $?The entries in bold were modified for our purposes, and the idea is that the /var/spool/filter directory contains both in.$$ and out.$$ files for each email, and a log of everything is kept in filter.log. Once a message has been identified as garbled, it's a simple matter to diff the input and the outputs: when it shows that only the header has been modified, and nothing in the body has, it's easy enough to be sure that SpamAssassin is not messing anything up.
But what if we want to really take SpamAssassin out of the loop, so it doesn't even add its few headers: this can be done on an ugly, ad-hoc basis for testing (though we're working on a much cleaner whitelisting system for production use).
The filter is typically called from Postfix with flags indicating sender and recipient, and we can use these to bypass SpamAssassin processing. We don't want to do real parsing on the command line, so our approach is to simply look for the trigger address anywhere in the command line. When we find one that matches, we simply exec sendmail directly: otherwise we run the mail through SpamAssassin.
...
echo "$$: running $@" >> filter.log
case "$@" in
*marketwatchmail.com*) exec $SENDMAIL "$@" ;;
*)
/usr/local/bin/spamc > out.$$ ||
{ echo "Message content rejected"; exit $EX_UNAVAILABLE; }
;;
esac
$SENDMAIL "$@" <out.$$
exit $?At this point my customer is convinced that SpamAssassin is not munging his messages, so we're going to set up a parallel sendmail system to find out if it's Postfix. We both suspect that it's Exchange, but we don't know why.
Well I have finally entered the 21st century: I'm now operating wireless.
I've had an old 400MHz Dell laptop that I used mainly for network testing, but I finally got an 802.11b wireless router and PCMCIA card, and I can't believe how much I love it. I mainly use it just to secure-shell to my Linux boxes and to do web surfing and IM, and it's plenty fast for that. I also fire up my RadioMX streaming music service and sit on the back porch laptopping with the backyard birds. The female scrub jay ate from my hand yesterday.
What really helped was getting good batteries: I got a killer price on two units from Pacific Battery Systems, and I get more than 8 real hours of life. They're having a special now on these batteries ($109 for 3800 mAh batteries). And they have 4460 mAh batteries available as well - these power densities are just amazing.
I've also done a bit of wardriving and am amazed how many systems close to me are wide open. With Netstumbler and my soon-to-arrive wardriving kit with external antenna, I should have quite a bit of fun.
Wireless rocks.
Now and then I get email from people asking for help with topics I've written about in my Tech Tips section, and I'm usually happy to lend a hand. Yesterday I got an email from a pleasant fellow asking about Hacking Sybase for the NT Administrator, but it was clear he wasn't reading the tip in my site: my tip was reproduced entirely at a security web site, with only my email address for attribution. Nobody had ever asked me about this, and though I don't really claim copyright, I still thought it was kinda rude.
Even though I figured I'd get nowhere, I sent off a note to the webmaster of the site, and it took no time to get a response: they had received this indirectly by a member submission, and they were not in the business of stealing content. They asked what I wanted done: remove the page? change the attributions? I just asked that they link to my main web site, and they had this done in less than an hour.
I thought I'd get blown off, but instead was blown away.
SecuriTeam, you're a class act. Thank you.
A customer has been bugging me for weeks go figure out how to get his SCO UNIX system to print to printers attached to XP computers on his network, and I've finally gotten around to making it work.
It concerns me that the answer is "enable the passwordless Guest account", but in the environment in question it happens not to be a concern. So as is the custom, a Tech Tip was born:
Tech Tip: Printing to XP local printers from Samba
CERT recently issued an advisory on the sendmail remote buffer overflow, and it looks very serious. Apparently, it can provide remote root access, doesn't leave any log entries for successful exploits, and because it's content-based, even mail servers "protected" behind invulnerable relays are still not safe.
A working exploit was released less than 24 hours later, and this underscores what the smart people in security say: "presume that all vulnerabilities are explolitable - don't wait for the public announcement". This is a very nasty vulnerability - run, don't walk, to take care of this.
Now might be a great time to migrate to a better mail server, such as QMail or (my favorite) Postfix. I've been spending the last day performing sendmail-to-Postfix migrations, and it's gone surprisingly smoothly. That we can also add SpamAssassin to the mix as a Postfix content filter is an added bonus.
But even those sticking with sendmail must patch this immediately.
 Yahoo! has long implemented means that prevent automated account-creation attempts: the pages display a word or number in an image and requiring the user to type it. Apparently, frustrating robots is pretty important, and it seems to be successful.
Yahoo! has long implemented means that prevent automated account-creation attempts: the pages display a word or number in an image and requiring the user to type it. Apparently, frustrating robots is pretty important, and it seems to be successful.
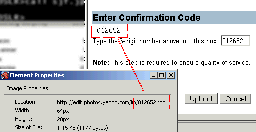
They have a similar approach when uploading an image in a Yahoo! member profile. A six-digit number is displayed in a JPEG image, but the overall implementation wasn't done quite right. Checking the properties of the image show that it wasn't done quite right:
(click the image to see a larger version)
By including the confirmation number as part of the image name, it means that automated programs would trivially be able to automate this. Oops.
In fairness to Yahoo!, this was apparently some kind of debugging mode, and they had it fixed within five hours of reporting. It's fun to imagine a collective "Doh!" from the security people.
 I recently purchased an HP OfficeJet d145 all-in-one fax/scanner/printer/copier, and it's excellent. It's got a flat-glass scanner plus a sheet feeder, so it does both copying and faxing very well. Print quality is great too.
I recently purchased an HP OfficeJet d145 all-in-one fax/scanner/printer/copier, and it's excellent. It's got a flat-glass scanner plus a sheet feeder, so it does both copying and faxing very well. Print quality is great too.
But this unit has separate printheads from ink cartridges, and it turns out that the full refill kit is six items retailing for more than $200. Each of cyan/magenta/yellow/black printheads are separate part numbers, and the color ink cartridge is separate from black. I'm not sure why they did this, but I suspect that the printheads can be of higher quality (because they last longer) than the ones embedded the ink cartridges. I can't figure out why they don't have a "printhead kit" with all four.
That the supplies are more than half the cost of the printer (the same kit goes in the lower-end units as well) suggest that HP's doing really well. It might be seen as a "ripoff", but more likely is that the printer costs much less than the unit itself would cost without the consumables being such a profit center.
But this is a great unit - I'd totally buy it again.

Recently I wrote about measuring performance of Ethernet print servers, and in the process ended up learning on of them in particular fairly well. I'd gotten about halfway through a tool for managing the family of ether printservers from Hawking Technology when the project decided that these weren't going to work for us, so I dropped it.
But figuring that somebody else out there may want to use these units under UNIX, I mostly finished the tool and the documentation, so it's no longer necessary to use the vendor-provided PSAdmin Windows tool to set the IP address parameters.
This has been tested with the H-PS1U Ether-to-USB printserver and the PN7127P Ether-to-Parallel printserver.
- Tech Tip: Working with Hawking USB and Parallel Ethernet Print Servers
- Tool: Hawking Print Server Configuration Utility
On Friday morning, I had to suddenly drive to northern California for a business meeting, and since it's a 6 hour drive from where I live just south of Los Angeles, I knew I needed something to keep my mind occupied. I'm a member of a book club at Talking Book World, so I dashed in to pick up a book on tape for my trip up.
I found Inventing the Middle Ages by Norman Cantor, and my five-second, in-a-big-hurry inspection suggested that this was a history in the Middle Ages, perhaps the development of technology. I love this stuff and thought it would be a delightful way to pass the time while driving those many miles through the middle of nowhere.
Not.
This was a history of the historians of the Middle Ages, and it was really, really awful. Not only was the subject matter totally uninteresting to me (e.g., I don't care about medieval scholars and their background which informed their perspective on the middle ages blah blah blah), but Cantor is a terrible writer.
Central California is a radio wasteland, so listening to this drivel was only slightly better than nothing. Once I reached San Jose, I went to Barnes & Noble and bought Who Says Elephants Can't Dance?", the story of how Lou Gerstner turned IBM around. Though I'm taken to understand that many IBMers consider it to be a self-serving book, it was at least very easy to listen to, and it made the 100 mph trip back home much more pleasant.
But never again will I grab a book for a long trip without really knowing what I'm getting.
![[SJF Logo]](../../images/sjflogo.gif)