Chapter 7
Security Concepts and Planning
In order to achieve the level of resource protection required by most corporate clients, careful security planning is required. The WorldDesk product family offers a variety of mechanisms to help customers reach a balance in the tradeoff between the level of security provided and the protection offered. In this section, security requirements and the WorldDesk configurations required to achieve resource protection goals are examined.
Planning
The first step in planning for WorldDesk security configuration is determination of needs. When doing this, remember a maximum of 256 users may be added to the security database for a Commuter-based cluster. However, there is NO limit to the number of users that may be included in the security database for a Comlink-based cluster. Security may be broken into three classes:
Planning for Dial-in Security
Dial-in security is usually the most critical concern of most organizations. Since WorldDesk is designed to allow remote users to gain full access to enterprise network resources via public switched telephone and digital network services, it is necessary to provide security to limit access to only desired clients.
"Dial-in security" refers to the security requirements placed on any client for which WorldDesk provides the ability to transmit and receive network packets via dial-up interface. Such clients are commonly called "remote node clients", and they transmit and receive packets via a dial-up bridge/router.
Examples of dial up bridge/router products include WorldDesk (when the remote node mode is enabled), Microsoft*s RAS product, and Novell*s NetWare Connect. The WorldDesk Server may be seamlessly used in conjunction with RAS and Connect. In such cases, the provision of dial-in security is the responsibility of the product providing dial-in services; WorldDesk provides security only for access to WorldDesk server resources.
In general, when a system is made more secure, either the costs of providing the security or the inconvenience to the remote user (or both) are increased. Thus, tradeoffs exist in determination of the level of security to be achieved and the willingness of the organization to accept the costs and inconveniences associated with that level of security.
Since the needs of WorldDesk users vary, WorldDesk provides for implementation of a number of security levels. The appropriate security level to be enacted must be determined by the system administrator by balancing the needs and costs as appropriate for the particular installation.
Password Security
WorldDesk always requires a minimum of User ID/password security for dial-in access to the enterprise LAN. This represents the entry level for security implementation. When password security is required, the remote user is required to provide a user name and password that can be authenticated by the WorldDesk Server. Authentication can be achieved using a number of different authentication servers; authentication servers are described later in this document.
Password security is easily understood by most remote users, and therefore requires little user training. At the time the connection to the network is made, WorldDesk prompts the user to enter his user name and password. Once a session is established, the WorldDesk Server internally assigns a unique identifier to the session and provides this identifier to the client software. The user is not provided with this information, and the identifier is allocated such that it is globally unique.
Sessions may involve multiple calls to the server in cases where the modem link is lost (for example, due to a noisy line) or suspended due to inactivity. The WorldDesk Server always validates the session identifier before allowing a session to be resumed. Additionally, a client may request that the server prompt for and revalidate a user ID and password on each call; this provides greater security at a slight user inconvenience. The added security prevents an unauthorized user from accessing a session on a remote machine for which the attended user is no longer physically present (such as an intruder that walks into an office while the original user is out).
Password prompting (always or at startup) is configured via the client configuration utility, and may be set on a client by client basis. The password assigned to a user account may be changed by the user with a provided WorldDesk utility. Distribution of this utility to users allows a system administrator to let users change their own passwords without gaining access to the WorldDesk Manager facility and without learning complex new interfaces.
The primary weakness of password security is that it may be compromised by "stolen" passwords. Passwords may be stolen via a line tap or via accidental or intentional disclosure. WorldDesk always encrypts passwords before transmission to make password stealing via line tap more difficult.
Challenge/Response Security
Challenge/response overcomes the weaknesses of password security at the cost of remote user inconvenience and additional hardware costs. Unlike other remote access products, WorldDesk Servers can provide challenge/response security without the addition of expensive server hardware. Remote users, however, are required to have a remote access token (a credit card sized hardware product) called the WorldDesk Remote Access Token.
Unlike password security, where the password transmitted over the line does not change from connection to connection, challenge/response security makes use of a random challenge generated by the server and an encrypted version of the challenge (the response) provided by the client. Since the challenge provided by the server changes on each call, the required response is different for each call. Hence, challenge/response is not subject to compromise via line tap.
When the user receives the random challenge provided by the server, the credit-card-like remote access token is used to encrypt the received challenge. The encryption algorithm used is called "DES". DES is a standard encryption algorithm developed by the United States National Institute of Science and Technology (NIST). Using even the most sophisticated Super Computers, DES is designed to be very difficult to "break" and is therefore very secure.
The DES algorithm uses an encryption "key" that is programmed into the remote access token to encrypt the challenge provided by the WorldDesk Server. The key is assigned so that each user has a different key. Once programmed into the remote access token card, the key may not be recovered (read back) from card. This ensures that a user cannot accidentally or maliciously disclose the key. A PIN number is required for successful use. When an incorrect PIN entry limit is reached, the internal key is erased by the token. This prevents a lost key card from being used by someone guessing the PIN number.
From a usage perspective, the dial-in user is prompted for a response to a challenge on each call to the server. The user enters the given number into the remote access token card, and enters the result displayed by the token into the appropriate field in the WorldDesk software pop-up box (see Figure 7 - 1). Challenge/response is fully integrated into WorldDesk; complex user operations are not required. In order to ensure the high degree of security afforded by DES challenge/response, a new response must be entered on each call to the server (for example, after a connection loss/resumption).
The DES algorithm is classified as a munition by the United States Department of State, and is therefore not exportable to all countries.

Figure 7-1, DES Challenge/Response Screen
Dialback Security
Dialback security provides for the WorldDesk Server calling a dial-in user back at a specified phone number on each call to the user. Dialback may be used in conjunction with any other security methods in use at the server and serves to further increase the level of security provided.
Since the WorldDesk Server places each call over which network packets are transmitted, the server "knows" the phone number at which the client is located. Since call forwarding is provided by many public telephone system carriers, the phone number does not necessarily ensure that the called location is known (although this may not be the case at most sites).
A side effect of dialback is that the telephone (analog or digital) lines at the server will bear all of the costs associated with the dial-in network access. At many organizations, this is the desired result. At others, however, this is unacceptable. In order to accommodate both cases, WorldDesk provides for three dialback settings: Prohibited, Optional, or Mandatory. These settings may be set via the User Administrator Properties screen shown in Figure 7 - 2. The "User Properties" screen may be accessed by right clicking on the Cluster icon and selecting the Security/User Management/Properties menu options.
When dialback is prohibited, the WorldDesk Server will never allow a client to use the dialback capability to reverse charges.
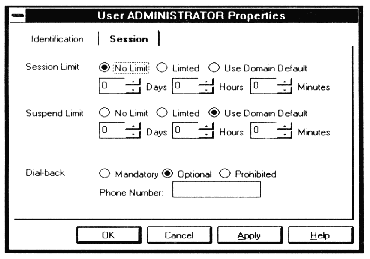
Figure 7-2, User Administrator Properties Screen
When dialback is optional, the remote user is allowed to select the callback number at dial-in time. This provides for charge reversal and provides a record of the number used for the session, but does not fix the callback number. Hence, the additional security offered by optional dialback is minimal.
When dialback is mandatory, the remote user is always called back at a number specified by the system administrator. This provides for both reversal of charges and additional security. The remote user may not override the dialback number specified by the administrator.
Planning for Dial-Out Security
Unlike access to the LAN via dial-in, many organizations do not require any security for on-LAN users to access shared modems for LAN dial-out purposes. WorldDesk dial-out security is therefore optional. Other organizations wish to restrict dial-out access to certain users or groups of users. The primary motivation for such restrictions is usually cost control for the calls placed on the lines or the potential for transmission of sensitive data to off-site destinations.
When dial-out (modem pool) security is enabled, only users that have dial-out privileges associated with their accounts may allocate ports at WorldDesk Servers. To verify the identity of such users, the WorldDesk Server requires users to provide a user name and password before granting access to modems. The user is prompted for this information via pop-up boxes provided by the WorldDesk client dial-out redirector (this maintains the ability to use off-the-shelf terminal emulation software with WorldDesk dial-out security).
Dial-out security is always based on passwords (rather than challenge/response). Dialback security is not involved in dial-out security, since there is no incoming dial-up call to be validated.
Planning for Management Access Security
Like dial-out security, management access security for WorldDesk Servers is optional. Many sites wish to allow any network user to operate the WorldDesk management facility, while others wish to restrict access to a system administrator.
The Cluster Properties screen (Figure 7 - 3), facilitates the varying needs of WorldDesk users, WorldDesk Servers may be configured to allow unrestricted access to management, to allow only designated users with a valid username/password to access management data, or to allow only the administrator account to perform management functions.
When management security is enabled, each operator may further be designated as having read-only privileges or read/write privileges. This capability is intended to allow read access to management data for a help desk, while only the system administrator is allowed to change the WorldDesk configuration.
Management security is always based on passwords (rather than challenge/response). Dialback security is not involved in management security, since there is no incoming dial-up call to be validated.
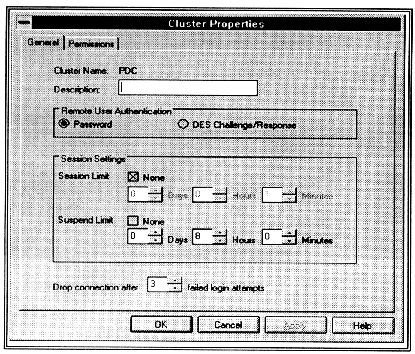
Figure 7-3, Cluster Properties Screen
Planning for Applink Session Security
The WorldDesk Server supports two levels of security pertaining to Applink clients; "Start Sessions" security, and "Override Rules" security.
An Applink client must be granted "Start Sessions" permission to initiate a remote control session on the server, regardless of the method used to start the session. Applink supports four modes of operation:
"Override Rules," is a further refinement on Applink security. If the Applink client does not have the "Override Rules" permission, a remote control session may not be initiated by the client using the run modes: "Run at the Server" and "Ask User". Thus, System Administrators can effectively limit the number of programs that may be run via remote control on a WinFrame‘ server, thereby conserving server resources.
Authentication Servers and the Security Database
In any security system, authentication depends on a key and an algorithm. The key represents a secret assigned to the user, and the algorithm is the method used to determine whether or not the user "knows" the secret. For example, in password security, the secret is a password known to the user and the algorithm is a simple comparison of the password provided by the user with one stored in a security database.
WorldDesk provides two classes of authentication methods: local methods, where WorldDesk provides both the algorithm and security database, and authentication server methods, where a system external to the WorldDesk software provides the algorithm and security database. The location of the security database influences both the fault tolerance characteristics and manageability of the system. The "Authentication Servers" screen (Figure 7 -4), is used to indicate which servers will be used as authentication servers. To access the "Authentication Servers" screen, right click on the Cluster icon and select the "Security/Authentication Servers" option.
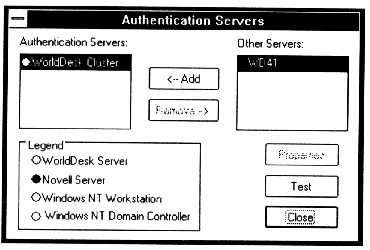
Figure 7-4, Authentication Servers Screen
Local Authentication Methods
Under the WorldDesk local authentication method, the WorldDesk Server both implements the authentication algorithm and maintains the security database. Local authentication methods implemented by WorldDesk include both password security and DES challenge/response security.
Because WorldDesk provides the security database for local authentication methods, it is necessary for a system administrator to add the necessary security information (user ID and password or DES key) into the security database using the WorldDesk management facility. This task is straight-forward, and is done on a cluster (rather than server) basis, as described later. This task, however, may be time consuming for customers with large user communities; authentication server methods may be more appropriate for such installations.
Authentication Server Methods
Under WorldDesk authentication server security methods, the WorldDesk Server consults an external security server to authenticate users. The authentication server is responsible for performing the authentication algorithm using a security database that it maintains. When an authentication server is used in conjunction with WorldDesk, it is not necessary to populate a local user database using the WorldDesk management facility. The database is managed through mechanisms provided by the authentication server.
Authentication servers are primarily beneficial in allowing multiple systems and applications to share a common security database. A common security database provides for a single repository for authentication information, and generally eases administrative chores associated with maintaining the database.
WorldDesk supports three types of authentication servers: Novell NetWare file servers, Windows NT servers/workstations and Windows NT Domain Controllers (see Figure 7 - 5). Multiple authentication servers may be configured for WorldDesk, in which case a user that is valid at any of the configured authentication servers is permitted access to WorldDesk resources.
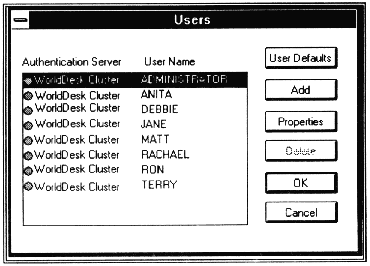
Figure 7-5
Users scrren Listing Authentication Server and Associated Users
Novellģ NetWare File Servers as Authentication Servers
When NetWare‘ is used as an authentication server, WorldDesk uses NetWare‘ Core Protocol (NCP) messages to consult the specified file server(s) to determine if a specified user name and password combination is valid. If the NetWare‘ server validates the specified user name and password, the user is allowed access to WorldDesk.
The NCP messages used by WorldDesk to communicate with the file server require NetWare‘ Bindery (3.1x servers) or Bindery Emulation (4.x servers) to be available at the file server. Additionally, passwords that are not encrypted must be enabled at the server. Time restrictions specified under NetWare‘ for an account may be enforced, but station restrictions and concurrent connection counts may not be used in conjunction with WorldDesk. NetWare‘ file servers do not support challenge/response security. Additionally, mandatory dialback security is not available because NetWare‘ does not support storing dialback numbers for user accounts.
Microsoft Windows NT as an Authentication Server
Systems running Microsoft Windows NT Server or Windows NT Workstation may also be used as authentication servers with WorldDesk NT-based systems. NT authentication servers are not currently supported by WorldDesk Commuter. When Windows NT is used as an authentication server, WorldDesk uses the Server Message Block (SMB) protocol to consult the specified Windows NT machine to determine if a specified user name and password combination is valid. If the Windows NT machine indicates that the specified combination is valid, the user is allowed access to WorldDesk.
When the Windows NT Domain Controller is specified as an authentication server, the NT domain user database is used as the security database. When an NT machine other than the domain controller is selected, the NT machine’s local security database is used.
Time restrictions specified under Windows NT for an account may be enforced, but station restrictions and concurrent connection counts may not be used in conjunction with WorldDesk. Additionally, mandatory dialback security is not available when using Windows NT as an authentication server because Windows NT does not support storing dialback phone number for user records.
Note that if more than one WorldDesk Comlink server is present in a cluster, an NT Workstation should not be used as an authentication server. An NT Domain Controller should be used instead.
Implementing WorldDesk Security
WorldDesk security is implemented on a WorldDesk cluster, rather than server, basis. This means that setting of a security option for the cluster causes all WorldDesk Servers in the cluster to be updated with the new setting. Cluster security helps to make the addition of new servers to a cluster simple, as the new server automatically obtains the cluster security settings when it is added to the cluster.
Once planning for security as described earlier in this section, has been completed, the WorldDesk Manager facility is used to set security options. Security options are set and changed dynamically and take effect immediately at all servers in the cluster. Security options may be changed without disrupting normal WorldDesk operations.
WorldDesk security setup is usually established through the following steps:
Further information on the details of using WorldDesk Manager to set security options is available through WorldDesk Manager*s online help facility. Use the toolbar option for help or press F1 in the menu for which further information is desired.
This document, and all Web contents, Copyright © 1997 by Cubix Corp., Carson City, NV, USA.